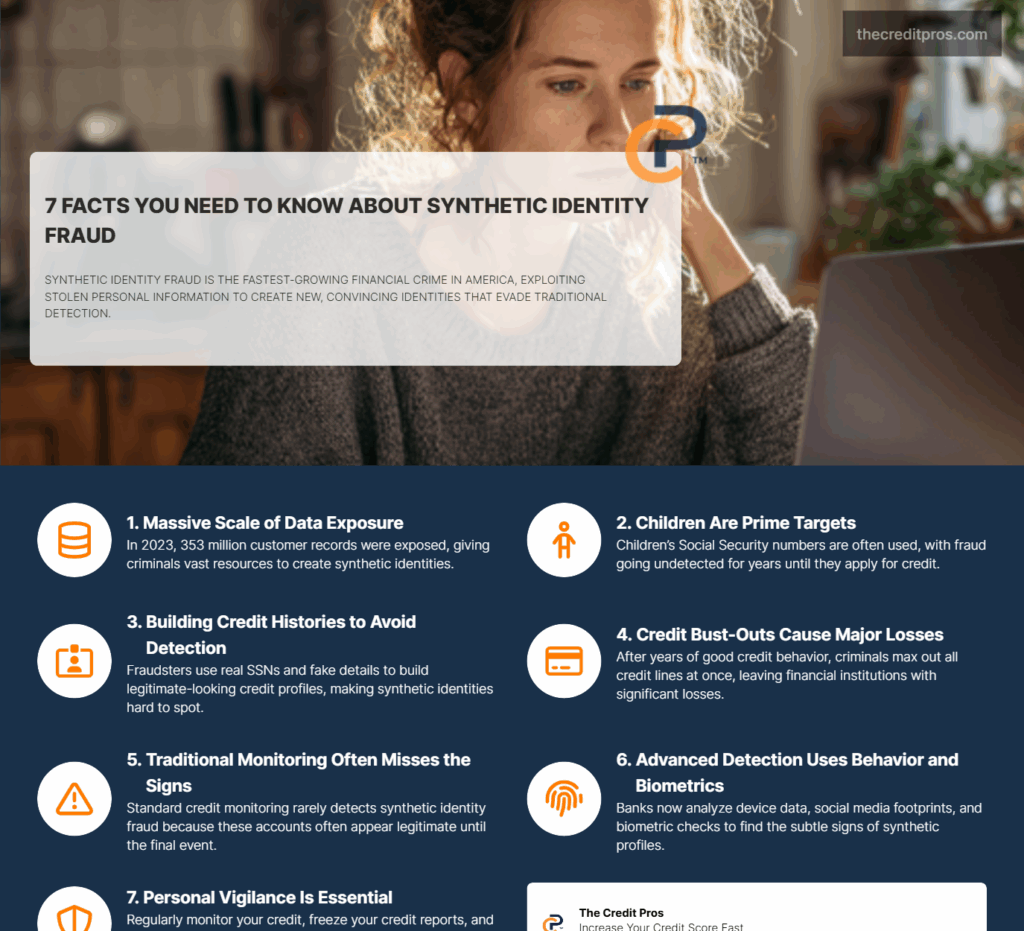
Synthetic identity fraud has quietly become the fastest-growing financial crime in America, with fraudsters stealing pieces of real people’s information to create entirely new, fake identities. Unlike traditional identity theft where criminals simply use your existing accounts, these sophisticated schemes involve building completely fabricated personas that can fool even the most advanced security systems. What makes this particularly dangerous is how these fake identities can remain dormant for years, slowly building legitimate credit histories before striking with devastating financial damage. Understanding synthetic identity fraud is essential for anyone concerned about financial security.

Many people are unaware of how prevalent synthetic identity fraud has become. The numbers tell a sobering story: with 353 million customer records exposed in data breaches last year alone, criminals have an endless supply of raw materials to construct these synthetic identities. Children are especially vulnerable since their stolen social security numbers won’t be discovered until they apply for their first credit card years later. But here’s what most people don’t realize – you might already be a victim without knowing it, and traditional credit monitoring often misses the warning signs entirely.
The Anatomy of Synthetic Identity Creation: Understanding the Criminal Blueprint
The sophisticated process of synthetic identity fraud begins with systematic data harvesting from the vast pools of compromised personal information available on the dark web and through data breaches. The Identity Theft Resource Center’s documentation of 353 million U.S. customer records exposed in 2023 represents just the tip of the iceberg for fraudsters seeking raw materials to construct fake identities. These criminals operate with methodical precision, understanding that certain data combinations create more believable synthetic profiles than others. Being aware of synthetic identity fraud can help individuals protect their information.
Fraudsters prioritize specific data points when assembling synthetic identities, with Social Security numbers serving as the foundation for their schemes. A legitimate SSN provides the critical government validation needed to pass initial screening processes, while fabricated names, addresses, and birth dates fill in the remaining profile details. The “Frankenstein” assembly method involves combining elements from multiple real individuals, creating identities that appear authentic when cross-referenced against individual databases but reveal inconsistencies when examined holistically across multiple data sources. To combat synthetic identity fraud, it’s crucial to understand the methods used by fraudsters.
Children represent the most valuable targets for synthetic identity creation because their SSNs remain dormant in credit systems for years before legitimate use begins. This extended window allows fraudsters to establish credit histories, open accounts, and build financial relationships without detection. By the time children reach adulthood and attempt to access credit for the first time, synthetic identities using their SSNs may have accumulated substantial financial activity, making the cleanup process extraordinarily complex and time-consuming. Awareness of synthetic identity fraud can prevent significant financial loss.
The reusability factor distinguishes synthetic identity fraud from traditional identity theft schemes. Once created, synthetic identities become permanent tools for application flooding, where criminals submit numerous account applications across different financial institutions simultaneously. This shotgun approach acknowledges that many applications will be rejected, but the mathematical probability ensures that some will succeed, providing fraudsters with multiple access points to the financial system. Every consumer should take steps to guard against synthetic identity fraud.
Geographic patterns in synthetic identity creation reveal regional vulnerabilities that criminals exploit strategically. Areas with high population turnover, limited local verification resources, or jurisdictions with less sophisticated fraud detection systems become preferred locations for establishing synthetic identities. Fraudsters often select addresses in these regions not because they have physical presence there, but because the local infrastructure makes verification more challenging for financial institutions. Understanding the nuances of synthetic identity fraud is essential for effective prevention.
The Credit Bust-Out Strategy: Long-Term Fraud That Builds Legitimate History
The credit bust-out strategy represents the most sophisticated evolution of synthetic identity fraud, requiring patience and strategic planning that can span multiple years. Fraudsters using this approach understand that immediate attempts to maximize credit lines trigger fraud detection systems, so they deliberately cultivate legitimate-appearing financial behavior over extended periods. This patient criminal approach involves making regular purchases, maintaining low balances, and establishing payment histories that mirror those of responsible credit users. Implementing strong defenses against synthetic identity fraud can safeguard your finances.
Credit line cultivation follows predictable patterns that fraudsters have refined through experience and shared knowledge within criminal networks. The initial phase typically involves securing low-limit credit cards or store cards that require minimal verification. Over 12-24 months, these accounts demonstrate consistent payment behavior, low utilization rates, and gradual balance increases that signal creditworthiness to automated scoring systems. Financial institutions respond predictably by offering credit line increases and pre-approved additional cards, exactly as the fraudsters intended. Strategies to combat synthetic identity fraud include ongoing monitoring and verification.
The “sleeper fraud” timeline reveals why traditional fraud detection methods often fail against synthetic identities. During the buildup period, synthetic identities exhibit better financial behavior than many legitimate customers, maintaining credit scores that can exceed 700 points. This counterintuitive reality creates a blind spot in risk assessment systems designed to flag high-risk behavior, not exemplary credit management. The synthetic identity’s stellar credit history becomes its most effective camouflage.
Maximum damage execution occurs when fraudsters coordinate the simultaneous activation of all available credit lines across multiple accounts and institutions. This final phase, known as the “bust-out,” can happen within days or weeks, with criminals maximizing every available dollar of credit with no intention of repayment. The timing is crucial because once the bust-out begins, fraud detection systems quickly identify the coordinated activity, but by then the damage is already complete. Businesses must also remain vigilant against synthetic identity fraud in their systems.
“Organizations that leverage a multi-layered approach that employs both manual and technological data analysis have the best chance to identify and mitigate fraud caused by synthetics, according to industry experts.” – Federal Reserve System
Behavioral patterns that distinguish legitimate credit building from synthetic preparation require sophisticated analysis to detect. Legitimate customers demonstrate organic spending patterns that reflect personal preferences, seasonal variations, and life events. Synthetic identities often exhibit more mechanical behavior patterns, with purchases that seem designed to maintain account activity rather than fulfill genuine consumer needs. These subtle differences become apparent only through advanced behavioral analytics that examine transaction patterns over time. Those who are aware of synthetic identity fraud can better protect their identities.
The psychology behind credit bust-out success lies in exploiting the trust-based nature of the credit system. Financial institutions profit by extending credit to reliable customers, creating inherent incentives to approve accounts that demonstrate good payment history. Synthetic identities exploit this fundamental business model by presenting exactly the profile that credit scoring algorithms are designed to reward, making detection extremely challenging without additional verification layers. Improving awareness and education is key to combating synthetic identity fraud.
Advanced Detection Signals: Beyond Traditional Red Flags
Multi-layered data inconsistencies provide the most reliable indicators of synthetic identity fraud when traditional red flags fail to surface. These inconsistencies often appear across seemingly unrelated data points that fraudsters struggle to coordinate perfectly. IP address analysis reveals when account applications originate from locations inconsistent with stated addresses, while mobile identifier tracking can expose when multiple identities share device fingerprints or cellular connections that legitimate individuals would never share. Knowing the risks associated with synthetic identity fraud allows for better preparations.
Social media footprint analysis has emerged as a critical detection tool because legitimate identities naturally accumulate digital breadcrumbs across platforms over time. Authentic individuals create social media accounts, interact with friends and family, post location-tagged photos, and engage in online communities in ways that synthetic identities cannot replicate convincingly. The absence of this organic digital presence, or the presence of hastily created profiles with minimal authentic interaction, signals potential synthetic fraud. Consumers should be proactive in addressing synthetic identity fraud issues.
Velocity and link analysis processes examine the connections and timing patterns that reveal coordinated fraud attempts. When multiple identities share the same address, phone number, or Social Security number, link analysis algorithms can identify these connections even when applications are submitted to different institutions. Velocity checks monitor the speed and frequency of applications, flagging unusual patterns such as multiple account requests from similar profiles within short timeframes. Staying informed about synthetic identity fraud can help reduce risks significantly.
The electronic Consent-Based Social Security Number Verification Service provides real-time validation that can immediately expose many synthetic identity attempts. This system checks whether Social Security numbers, names, and birth dates match official records, creating a critical verification checkpoint that fraudsters struggle to circumvent. However, sophisticated criminals have learned to use legitimate SSNs with fabricated personal details, requiring additional verification layers beyond SSN validation alone.
Biometric and liveness detection technologies represent the cutting edge of synthetic identity prevention, particularly for online account opening processes. Facial recognition systems can identify when multiple applications use the same individual’s biometric data with different identity information, while liveness detection ensures that biometric submissions come from physically present individuals rather than photographs or videos. These technologies create significant barriers for synthetic fraud schemes that rely on fabricated or borrowed identity credentials.
Machine learning algorithms excel at identifying anomalies in behavioral data that human reviewers consistently miss. These systems analyze thousands of data points simultaneously, recognizing subtle patterns that indicate synthetic fraud even when individual data elements appear legitimate. The algorithms continuously learn from new fraud attempts, adapting their detection capabilities to counter evolving criminal tactics. Fighting against synthetic identity fraud is a collective effort that requires vigilance.
Multi-Source Verification Defense System: Building Comprehensive Protection
Risk-based adaptive verification creates dynamic security protocols that adjust verification requirements based on real-time risk assessment. This approach recognizes that not all identity verification scenarios require the same level of scrutiny, allowing legitimate customers to experience streamlined onboarding while subjecting high-risk applications to enhanced verification procedures. The system evaluates multiple risk factors simultaneously, including data consistency, behavioral patterns, and historical fraud indicators to determine appropriate verification levels.
Cross-reference data integration leverages multiple databases and information sources to create comprehensive identity profiles that are difficult for synthetic identities to replicate. This approach goes beyond traditional credit bureau data to include utility records, employment verification, address history, and public records that legitimate individuals naturally accumulate over time. The integration process identifies discrepancies and gaps that synthetic identities typically exhibit when examined across multiple data sources.
Ongoing transaction monitoring extends fraud detection beyond the initial account opening process, recognizing that synthetic identities may remain dormant for extended periods before activation. Continuous behavioral analytics examine spending patterns, transaction timing, geographic consistency, and account usage that can reveal synthetic fraud even after successful initial verification. This monitoring becomes particularly critical during the months preceding potential bust-out events when synthetic identities may exhibit subtle behavioral changes.
The Federal Reserve System recommends a five-stage prevention workflow that provides a systematic approach to synthetic identity detection:
- Customer Onboarding: Collect and verify identity information using document verification and biometrics
- Real-Time Screening: Cross-reference data with multiple sources and implement machine learning models for anomaly detection
- Transaction Monitoring: Continuously monitor account activities using behavioral analytics to detect suspicious patterns
- Adaptive Verification: Adjust verification levels based on ongoing risk assessment and require additional checks for high-risk transactions
- Ongoing Compliance: Regularly review and update compliance measures while conducting periodic audits and assessments
Balancing fraud prevention with customer experience requires careful calibration of verification processes to avoid creating unnecessary friction for legitimate customers. The most effective systems use risk-based approaches that subject only suspicious applications to enhanced verification while allowing clearly legitimate customers to proceed with minimal additional requirements. This balance is achieved through sophisticated scoring algorithms that can distinguish between legitimate and synthetic identities with high accuracy.
Strategic implementation of AI and machine learning in real-time anomaly detection involves training algorithms on vast datasets of both legitimate and fraudulent identity patterns. These systems learn to recognize subtle indicators that human analysts might miss, such as typing patterns during online applications, mouse movement behaviors, or timing inconsistencies that suggest automated form completion. The AI systems continuously refine their detection capabilities as they encounter new fraud attempts and legitimate customer behaviors.
Personal Protection Strategies: Safeguarding Your Identity in a Synthetic Fraud Landscape
Proactive credit monitoring requires understanding the specific indicators that may suggest your personal information has been incorporated into synthetic identity schemes. Unlike traditional identity theft where unauthorized accounts appear directly on your credit report, synthetic fraud may manifest as inquiries for accounts you didn’t apply for or credit activity associated with variations of your personal information. Regular monitoring should focus on identifying hard inquiries from unfamiliar institutions, new accounts with similar but not identical personal details, and credit report discrepancies that suggest your SSN is being used with alternative names or addresses.
Identity freezing and fraud alerts serve as preventive measures that can significantly reduce your vulnerability to synthetic identity fraud. Credit freezes prevent new accounts from being opened without your explicit authorization, effectively blocking fraudsters from using your SSN to establish synthetic identities. However, the effectiveness of freezes depends on consistent implementation across all three major credit bureaus and understanding that some legitimate transactions may require temporary freeze removal.
Digital footprint management involves controlling the amount and type of personal information available online that fraudsters can harvest for synthetic identity creation. This includes reviewing social media privacy settings, limiting the personal details shared on professional networking sites, and being cautious about providing personal information to online services that may not have robust data security measures. The goal is not complete digital anonymity but rather reducing the availability of personal information that can be combined with other data to create convincing synthetic profiles.
Recovery and remediation from synthetic identity fraud requires a systematic approach that differs significantly from traditional identity theft recovery. When your information has been used in synthetic schemes, the fraudulent accounts may not appear on your credit report, making detection more challenging. Recovery involves working with credit bureaus to identify and remove any synthetic accounts, coordinating with law enforcement when criminal activity is suspected, and implementing enhanced monitoring to prevent future synthetic use of your information.
The distinction between traditional identity theft and synthetic fraud becomes crucial when reviewing credit reports and identifying potential victimization. Traditional identity theft typically shows unauthorized accounts or transactions directly linked to your existing credit profile. Synthetic fraud may appear as credit inquiries for accounts that don’t subsequently appear on your report, variations in how your name or address appears in credit files, or accounts that share your SSN but have different personal details.
Legal protections and rights available to synthetic identity fraud victims vary significantly from those covering traditional identity theft. The Fair Credit Reporting Act provides certain protections, but synthetic fraud cases often fall into gray areas where the fraudulent accounts may not directly impact your credit score or appear on your credit report. Understanding these legal distinctions helps victims navigate the recovery process and access appropriate remediation resources.

Conclusion: The New Reality of Identity Protection
Synthetic identity fraud represents a fundamental shift in how we must approach personal financial security, moving beyond traditional credit monitoring to comprehensive identity protection strategies. The sophisticated nature of these schemes—where criminals patiently build legitimate credit histories before executing devastating bust-outs—demands equally sophisticated defense mechanisms that combine multi-layered verification systems, continuous behavioral monitoring, and proactive personal vigilance. The fight against synthetic identity fraud continues to evolve and adapt.
Ultimately, understanding and addressing synthetic identity fraud is crucial for safety. While the 353 million exposed customer records from last year provide criminals with endless raw materials, understanding their methodical approach to identity construction gives you the knowledge needed to recognize and prevent these attacks. Understanding synthetic identity fraud and taking action can help prevent future issues.


