In a digital economy where your financial identity is constantly at risk, credit monitoring essentials have become important rather than optional. Every day, thousands of Americans face the consequences of credit fraud—damaged scores, financial losses, and the stress of recovery that can take months or even years. What specific warning signs should you watch for regarding credit monitoring essentials? And how quickly does monitoring actually need to happen to prevent serious damage?
Your credit profile represents years of financial decisions and affects everything from mortgage rates to job opportunities. This guide breaks down the practical steps to protect this valuable asset through both digital and physical safeguards. We’ll examine how the three major credit bureaus track your financial activity, evaluate which monitoring services deliver real protection versus false security, and provide a clear response protocol for when suspicious activity appears. The difference between effective credit monitoring and basic awareness could save you thousands of dollars and countless hours of frustration.
Implementing credit monitoring essentials is a proactive step to mitigate risks and enhance financial security.
The Anatomy of Credit Monitoring: Beyond Basic Vigilance
Understanding credit monitoring essentials allows individuals to respond swiftly to potential threats.
Investing in credit monitoring essentials is crucial for maintaining a healthy credit profile.
Staying informed about credit monitoring essentials can empower you to take control of your financial situation.
By prioritizing credit monitoring essentials, you can safeguard yourself against financial setbacks.
Utilizing credit monitoring essentials enables you to detect irregularities early.

Credit monitoring goes far beyond simply checking your credit score occasionally. It represents a proactive approach to financial security that requires understanding both the visible and invisible elements affecting your credit health. While many consumers believe they’re adequately protecting themselves by reviewing their credit reports annually, true monitoring involves continuous vigilance of multiple data points that signal potential threats.
Understanding credit monitoring essentials is key to safeguarding your financial future.
Credit bureaus collect an extensive array of information that influences your credit profile. Beyond the obvious factors like payment history and credit utilization, they track public records, address changes, new account applications, and even inquiries that don’t result in new accounts. These hidden data points create a comprehensive financial fingerprint that monitoring services scrutinize for inconsistencies. When unusual patterns emerge—such as a new account opening in a state where you don’t reside or a sudden spike in credit utilization—effective monitoring systems flag these anomalies immediately. Learning about credit monitoring essentials can help you recognize these important patterns.
The distinction between passive awareness and active monitoring becomes critical when understanding response timelines. Credit fraud can escalate rapidly, with damage multiplying within hours of initial unauthorized access. Active monitoring provides real-time alerts about suspicious activities, allowing you to intervene before significant damage occurs. For instance, when monitoring detects an unauthorized hard inquiry, you can place immediate freezes on your credit reports, potentially preventing fraudsters from opening accounts in your name. This early intervention can mean the difference between a minor inconvenience and months of credit rehabilitation.
Specific red flags that quality monitoring should identify include:
- Unusual hard inquiries from unfamiliar lenders
- New accounts appearing that you didn’t authorize
- Sudden changes in credit utilization ratios
- Address changes or updates to personal information
- Payment delinquencies reported on accounts in good standing
- Unexpected changes to credit limits or account statuses
The relationship between detection speed and financial impact cannot be overstated. Research consistently shows that the longer fraud goes undetected, the more severe the financial consequences become. While basic credit awareness might alert you to problems weeks or months after they occur, comprehensive monitoring narrows this window to hours or days. This compressed timeline provides critical advantages in limiting liability, preserving credit scores, and reducing the administrative burden of resolving fraudulent activity.
Focusing on credit monitoring essentials helps ensure a proactive approach to financial security.
Effective credit monitoring essentials can make a significant difference in your financial resilience.
Implementing credit monitoring essentials should be part of your financial strategy.
Regularly reviewing credit monitoring essentials can prevent potential fraud.
Embracing credit monitoring essentials enhances your financial awareness.
Following credit monitoring essentials can help diminish the impact of fraud.
Integrating credit monitoring essentials into your routine can enhance your security measures.
Building Your Digital Fortress: Technical Safeguards
Recognizing the importance of credit monitoring essentials is vital for every consumer.
By committing to credit monitoring essentials, you take an active role in your financial health.
Establishing credit monitoring essentials can significantly reduce risks associated with fraud.
Managing your credit monitoring essentials effectively promotes financial stability.
Being proactive about credit monitoring essentials is key to vulnerability management.
Engaging with credit monitoring essentials helps you make informed decisions about your finances.
In today’s interconnected financial ecosystem, implementing robust technical safeguards forms the foundation of effective credit protection. Multi-factor authentication (MFA) stands as perhaps the most crucial defense mechanism for your financial accounts. By requiring something you know (password), something you have (mobile device), and sometimes something you are (biometric verification), MFA creates multiple barriers against unauthorized access. When implementing MFA, prioritize financial services directly connected to your credit profile—banking portals, credit card accounts, and credit bureau access points should all utilize this additional security layer.
Password management represents another critical component of your digital fortress. The days of using simple, memorable passwords across multiple financial platforms have long passed. Each credit-related service requires a unique, complex password containing a minimum of 12 characters with a mix of uppercase letters, lowercase letters, numbers, and special symbols. Password managers provide an efficient solution for generating and storing these complex credentials without creating vulnerability through written records or digital files. Additionally, establishing a regular schedule for password rotation—ideally quarterly—adds another layer of protection against credential theft.
Secure device practices extend beyond password management to encompass comprehensive digital hygiene. Financial activities should only be conducted on devices with current operating systems and security updates. Public Wi-Fi networks present significant vulnerabilities for financial transactions; using cellular data or a virtual private network (VPN) creates an encrypted tunnel for sensitive information. Furthermore, dedicated devices exclusively used for financial management provide maximum security by limiting exposure to potentially compromised websites or applications. These devices should maintain minimal software installations, focusing solely on essential financial management tools.
Digital hygiene protocols must address both technical and behavioral aspects of security. Regular scanning for malware, particularly keyloggers that capture password entries, provides essential protection. Browser security requires equal attention—extensions and plugins should undergo rigorous vetting before installation, as malicious add-ons can capture financial data during transactions. Clearing browser caches and cookies after financial sessions prevents persistence of sensitive information, while enabling automatic logout features ensures accounts close properly when inactive.
Understanding credit monitoring essentials allows you to navigate financial challenges effectively.
Transaction security relies heavily on encryption protocols that protect data in transit. When accessing financial portals, verify the presence of HTTPS in the URL and a lock icon in the browser address bar, indicating secure communication. For maximum protection, consider implementing a dedicated email address used exclusively for financial communications, reducing the likelihood of phishing attempts reaching your primary inbox. This specialized email account should utilize additional security measures, including complex passwords and limited sharing, creating a protected channel for legitimate financial alerts and notifications.
Physical Safeguards: Protecting Your Tangible Credit Assets
Despite our increasingly digital financial world, physical credit assets remain vulnerable entry points for fraud. Modern techniques for safeguarding physical credit cards extend beyond basic vigilance to strategic management of these tangible assets. RFID-blocking wallets and card sleeves prevent electronic skimming of contactless cards, protecting against a sophisticated theft method that leaves no physical evidence. Additionally, strategically positioning cards within wallets—placing high-value credit cards in less accessible sections—creates an additional barrier against pickpocketing and opportunistic theft.
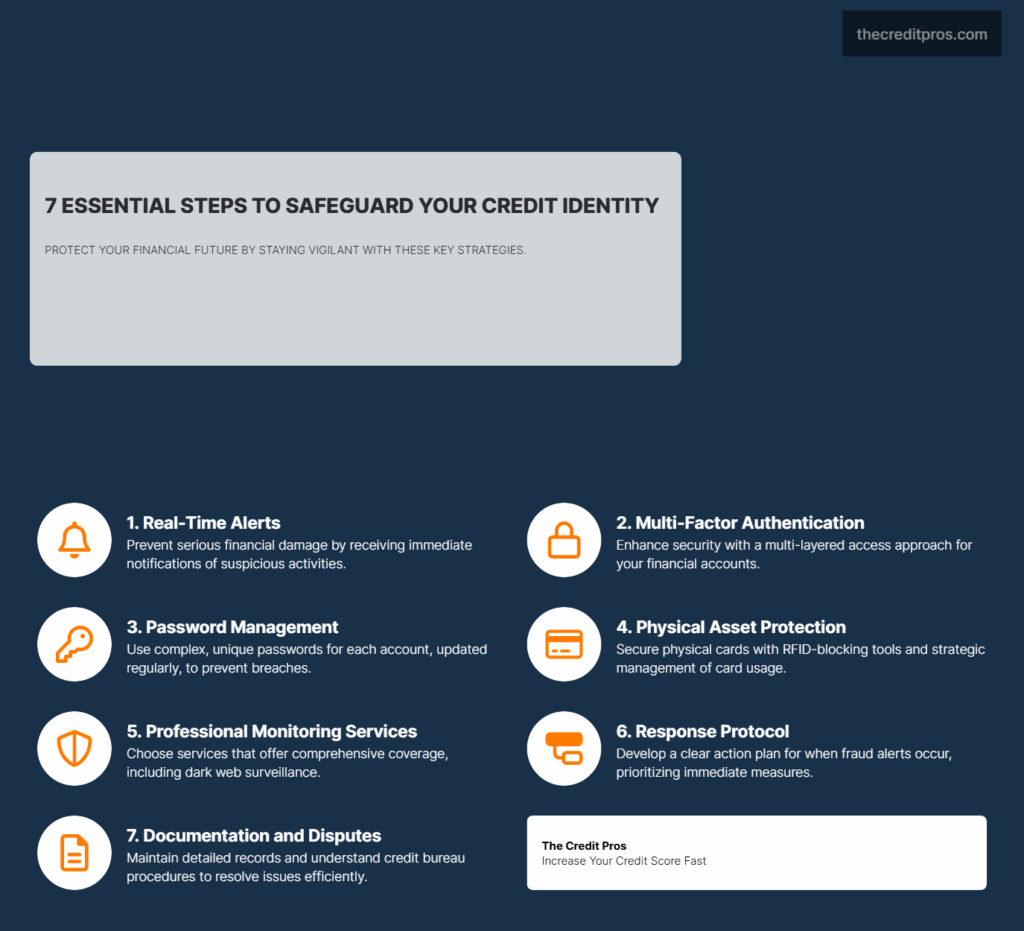
Strategic management of card expiration and replacement requires proactive planning rather than reactive responses. Create a digital calendar with alerts for upcoming expirations, scheduling reminders 30-45 days before cards expire. This timeline allows for addressing potential mail delivery issues without service interruptions. When replacement cards arrive, implement immediate activation followed by secure destruction of expired cards using cross-cut shredders that render magnetic strips and chips unreadable. For maximum security, some consumers maintain a dedicated shredder exclusively for financial documents, preventing cross-contamination with general recycling.
Secure disposal extends beyond expired cards to encompass all physical documents containing financial information. Pre-approved credit offers, account statements, and even seemingly innocuous receipts can provide valuable data for identity thieves. Implement a three-tier document management system: immediate shredding for non-essential documents containing personal information, secure short-term storage for documents needed for tax purposes, and vault storage for permanent records. This systematic approach prevents accumulation of vulnerable documents while ensuring necessary records remain accessible.
Creating a personal system for tracking card usage provides an additional layer of protection against unauthorized charges. Dedicated transaction journals or secure digital logs allow for regular reconciliation between personal records and official statements. This practice not only identifies potential fraud but also catches billing errors that might otherwise go unnoticed. Some consumers implement a rotation system for credit cards, designating specific cards for particular merchant categories, which simplifies monitoring by establishing clear usage patterns that make anomalies more apparent.
Ultimately, credit monitoring essentials contribute to a robust financial defense.
Virtual card numbers represent a powerful tool for online purchases, creating disposable payment credentials linked to your actual account. These temporary numbers can be limited by transaction amount, merchant, or time period, significantly reducing exposure during online shopping. Most major credit card issuers now offer this feature through their online portals or mobile applications. For maximum protection, consider using single-use virtual numbers for unfamiliar merchants and dedicated merchant-specific virtual cards for recurring subscriptions, allowing immediate cancellation if compromised without affecting other services.
Prioritizing credit monitoring essentials is essential for long-term financial success.
Incorporating credit monitoring essentials ensures you are prepared for potential issues.
Leveraging Professional Monitoring Services: What to Look For
Professional credit monitoring services vary significantly in both scope and effectiveness, making evaluation criteria essential for selecting appropriate protection. Premium services should monitor all three major credit bureaus simultaneously, providing comprehensive coverage across the credit reporting ecosystem. Additionally, effective services extend monitoring beyond credit reports to include dark web surveillance, public records, and non-credit identity indicators. This multi-layered approach identifies threats before they manifest in credit reports, providing crucial early warnings of potential identity compromise.
When conducting a cost-benefit analysis between free and paid monitoring services, consider both coverage breadth and response capabilities. Free services typically monitor a single credit bureau with limited alert options and delayed notifications. While these basic services provide some protection, they often miss critical warning signs visible only through comprehensive monitoring. Premium services justify their cost through expanded coverage, real-time alerts, and remediation assistance. Many paid services include identity theft insurance, covering recovery costs that can exceed thousands of dollars, along with dedicated fraud resolution specialists who navigate the complex recovery process.
Understanding the limitations of automated alerts prevents developing a false sense of security. Most monitoring services operate on predefined thresholds that may not align with individual financial patterns. For instance, standard alerts might flag a $5,000 purchase as suspicious, but miss a pattern of smaller unauthorized transactions that collectively indicate fraud. Additionally, monitoring services cannot detect certain fraud types, such as synthetic identity theft where criminals combine your Social Security number with fabricated information to create new identities. Recognizing these blind spots allows for implementing complementary protection measures rather than relying exclusively on automated systems.
Interpreting monitoring notifications requires understanding both the alert context and appropriate response protocols. Notifications typically include severity indicators that guide response urgency—distinguishing between informational notices and critical alerts requiring immediate action. When receiving alerts, verify the triggering activity through direct contact with the reporting institution rather than responding through links in the notification itself, which could be sophisticated phishing attempts. Establish verification protocols using official contact information obtained independently from the notification to ensure communication authenticity.
Customizing alert thresholds to match personal financial patterns significantly improves monitoring effectiveness. Most premium services allow adjustments to notification parameters based on individual spending habits and risk tolerance. Travelers should temporarily adjust geographic restrictions during planned trips, while infrequent shoppers might lower transaction amount thresholds to catch unusual purchases. Seasonal shoppers can temporarily increase spending thresholds during holiday periods to reduce false positives. This personalization transforms generic monitoring into tailored protection aligned with specific financial behaviors, dramatically improving both security and user experience.
Creating Your Response Protocol: When Alerts Strike
Developing a comprehensive response protocol transforms the chaotic aftermath of fraud detection into a methodical recovery process. The foundation of this protocol begins with categorizing alerts by severity and establishing corresponding action timelines. Critical alerts—such as new account openings or address changes—require immediate response, often within minutes or hours of detection. Secondary alerts, like unusual purchase patterns on existing accounts, typically allow slightly longer response windows but still demand attention within 24 hours. For maximum effectiveness, document this protocol as a written action plan stored both digitally (in encrypted format) and physically in a secure location, ensuring accessibility even if digital systems become compromised.
Timeline considerations become crucial when prioritizing response actions. Within the first hour of detecting serious fraud, contact the affected financial institutions through their dedicated fraud departments, place initial fraud alerts with all three credit bureaus, and begin documenting the incident details. Within 24 hours, file police reports, extend fraud alerts or implement credit freezes, and notify secondary accounts that might be affected. Within the first week, follow up on all initial reports, request new cards with different numbers, change passwords across all financial platforms, and begin the formal dispute process with credit bureaus. This tiered approach ensures critical protective measures activate immediately while allowing time for thorough documentation of more complex recovery steps.
Proper documentation serves as the foundation for successful resolution with both credit bureaus and law enforcement. Create a comprehensive fraud file containing chronological records of all suspicious activities, copies of alerts received, transaction details, and communication logs with financial institutions. When filing police reports, provide specific details rather than general statements—exact dates, transaction amounts, and merchant information significantly improve investigation quality. Most credit bureaus now accept digital submissions of supporting documentation, but maintain original copies of all materials submitted. This documentation not only supports immediate dispute resolution but also provides critical evidence if extended remediation becomes necessary.
Navigating the dispute process with credit bureaus requires understanding their specific procedures and timeframes. The Fair Credit Reporting Act mandates that bureaus investigate disputes within 30 days, but effective resolution often requires strategic communication. When submitting disputes, reference specific items rather than filing general fraud claims, and include supporting documentation that directly addresses each disputed item. Maintain regular contact with investigators throughout the process, documenting all communication attempts and responses. If initial disputes receive unsatisfactory resolutions, escalate through supervisory channels rather than simply resubmitting identical information, as repeated similar disputes may be classified as frivolous.
Rebuilding affected aspects of your credit after a security incident requires both patience and strategic planning. Begin by establishing new accounts with enhanced security features, including verbal passwords and account activity notifications. Consider securing these new accounts with credit freezes that temporarily lift only when you initiate legitimate applications. Monitor credit reports weekly during the first three months following the incident, gradually extending to monthly reviews as recovery progresses. Some consumers find secured credit cards useful during this rebuilding phase, as they provide active credit reporting with minimal risk exposure. Throughout this process, maintain detailed records of all recovery actions, creating documentation that supports rapid response if subsequent fraud attempts occur.
Conclusion: Vigilance as Your Financial Shield
Credit monitoring has evolved from a luxury to a necessity in our digital financial landscape. The multi-layered approach outlined—combining technical safeguards, physical protections, professional services, and response protocols—creates a comprehensive defense system against increasingly sophisticated threats. Effective monitoring doesn’t just alert you to problems; it provides the critical time advantage needed to minimize damage when breaches occur. The distinction between basic awareness and active monitoring often determines whether fraud becomes a minor inconvenience or a years-long recovery process.

Your credit profile represents more than just numbers—it’s the culmination of your financial decisions and a gateway to future opportunities. The investment in proper monitoring pays dividends through lower interest rates, insurance premiums, and protection against potential losses. While no system guarantees complete security, implementing these strategies dramatically shifts the odds in your favor. Remember: in the realm of credit protection, you’re not just defending numbers on a report—you’re protecting your financial identity in a world where that identity has become as valuable as any physical possession you own.


